Rounding errors
Wendy M Grossman comments on the US's use of surveillance drones over US soil

The key purpose of the long-running Computers, Freedom, and Privacy is to look ahead at developing technology and identify future conflicts. This year made earlier years seem startlingly prescient; the angry distrust of government breaking out all over the US since the PRISM revelations mirrors CFP in the mid-1990s, when it was home to the battles for the right to use strong cryptography to protect communications.
Crypto is, of course, also digital cash, which failed then but is now finding some traction in the form of Bitcoin. Last month, the state of California issued a cease-and-desist order against the Bitcoin Foundation, doubtless the first of many new rounds of disputes. In discussion, J. Bradley Jansen asked the Bitcoin panel, Is it a currency, a security, or a value transfer mechanism? Patrick Murck, general counsel for the Bitcoin Foundation, had the obviously right answer: "It's an experiment."
You could also call it a "rounding error" in the global economy. Bitcoin: $1.5 billion. Global economy: $50 to $60 trillion. But this term didn't pop up until later, when the topic was drones. This panel showed clearly that drones are at approximately the 1980s stage of personal computers: the ethos of the hobbyist Homebrew Computer Club is clearly echoed by the DC Area Drone User Group.
In the panel I moderated on PRISM, the security consultant Ashkan Soltani pointed out we have in fact four programs to worry about.
But let's go back to Bitcoin: it's it is not an answer. Under the current design of centralized exchanges and wallets, transactions are traceable. No matter how you parse the authorities' recent actions, even an experiment is going to attract the regulator's eye when it reaches the size and visibility where ordinary consumers might start dropping money into it expecting it to be safe. And most consumers will want it to.
But, as Murck said, regulators are struggling to understand Bitcoin, which doesn't operate like existing financial services: there's no controller and no one to hold responsible for transactions; it's not anonymous though it is private; and transactions are irreversible.
"Regulators think that's unfriendly to consumers," Murck said on Wednesday. "But it has a growing place in ecommerce." Wryly, he described lobbying as the big Bitcoin investment opportunity. "We need a sane regulatory environment for financial technology in general, not just Bitcoin," he said.
Personally, I suspect that regulators' are also confused by Bitcoin's arcane nature. A frequent flyer mile is equally abstract but maps mentally to something familiar. Perhaps Bob Newhart, a former accountant, could take on explaining Bitcoin the way he did Sir Walter Raleigh's discovery of tobacco.
Surprisingly, the situation with respect to drones is little different. Matthew Lippincott commented that in the public imagination a drone carries a camera and a gun. In fact, this isn't my image at all. On the sinister side, I immediately see the crop-dusting planes chasing Cary Grant in Alfred Hitchcock's North by Northwest. More benignly, my mental image is more like the small, light, radio-controlled helicopters that Think Geek sells. (You can tell I've led a sheltered life.) The reality, said Timothy Reuter is a "loud, flying lawnmower" that has to have its battery swapped out after 20 minutes.
So there was the question: do we look ahead to when drones are tiny bee-like things or even smaller molecular devices that may surveille us from within after we inhale them, or do we regulate for the clumsy, limited devices we have now?
Benjamin Wittes argued that the two topics - regulating drones and privacy - should be separated for regulatory purposes, arguing that Congress would be a better choice of regulator than the Federal Aviation Authority. "There's a pretty big societal change that is the ability of individuals to spy on other individuals in a way that we're really used to associating with governmental power," he said. "I think drones are a rounding error on that problem." A few minutes later, Lippincott agreed: "Surveillance is a rounding error in the problem of universal cameras and camera access that we're facing."
A regulator's lot is not an easy one. If you regulate a rounding error-sized problem people think you've lost all sense of proportion and are trying to impede innovation and experimentation. If you wait until the problem is a significant size, you're so far behind the technology that either people mock you or they have deliberately pre-empted any actions you might take. The point is not who was right when - although the ACLU gets points for its 2006 map of the NSA's spying capabilities. The point is which are the right fights to pick. The crypto wars of the mid-1990s. which Matt Blaze reviewed in his keynote, were a necessary but not sufficient battle to win. We - all of us - lost most of the war to preserve the confidentiality of communications. Partly, the issue is usability: people only use crypto when it's invisibly embedded in the infrastructure; if it's visible to consumers its use is too painful - and it's no defense against traffic analysis. The battle we won was a rounding error on the ones we lost. We need to be smarter.
Wendy M. Grossman’s Web site has an extensive archive of her books, articles, and music, and an archive of earlier columns in this series. Stories about the border wars between cyberspace and real life are posted occasionally during the week at the net.wars Pinboard - or follow on Twitter.
Image: Red tail hawk looking from lunch by TheJavierNavarro CC BY-NC 2.0
The future of home entertainment?
With the pending release of Xbox One, potential owners express some of their concerns about its new features.

As a member of Sheffield University Gaming Society (Slugs)for the last few years, as well as a lifetime gamer, I have seen a heavy transition from physical media to digital, from the good of Steam, to the bad of Sim City. Digital rights are fast becoming a hot topic for our members and other gamers due to the recent news of the Xbox one requiring online activation of all games, and requiring permanent online connection. Mix this with the privacy issues of a permanently connected camera, and you have the foundation for a potential PR disaster.
Before discussing the rights of the media however, I want to briefly summarise my own views on the permanently connected Kinect. Microsoft are touting this as an interaction requirement due to the heavily tied in voice commands. However this isn't strictly speaking true, and some of our members have voiced concerns about what they could be seeing, for example I have found news stories on patents for tailored advertisement. Combine these with the recent changes to Skype that allow snooping on the once secure system, and suddenly Microsoft's intentions seem to become clear: they want to know what your doing, when and how, 24/7, hopefully just for advertising purposes.
So clearly the Kinect alone breaches what some would consider their rights of privacy, but what about digital rights? In recent years we have seen an influx of games that require online activations especially for the PC. For me personally, this becomes a breach of rights when the company has the ability to pull the servers (as EA have done many times) and leaving you no longer able to access your game. So do modern games actually class as buying a game, or are we simply buying access for X amount of months/years? Does this break our rights as consumers and gamers to be sold a game that access can be removed in as little as a years time? Compare this to the pre internet era, I personally have PC games and console games from the 1990s that require me to simply install and input a cd key- my access can never be removed as there is no activation server used (although Gamespys recent closure does remove many older games Multiplayers).So can it really be justified that it is fair and proper to use these activation servers to stop piracy, when all they normally stop is pirates being able to play online, while more importantly, penalising the paying customers?
A more extreme example of digital rights breach is that of the recent Sim City, a game that requires you to permanently be connected and of which the developers have made it quite clear it will never work offline. Even during the initial heavily criticised weeks, where server access was sketchy at best, they still held still on the practice, why? I believe simply because of the DLC advertising EA has been making with the game. So with the quite heavy server load expected from all those users being permanent connected, it can be presumed that the servers will eventually be pulled and the game will quite literally be a paper weight. This example shows just how extreme this idea of just buying access can get.
So to return to the overall topic, the Xbox One, aside from the Kinect issue, Microsoft recently announced they would require on the spot checks at 'random' times to check if a game is new rather then pre owned. With most PC gamers, pre owned games are not a huge problem, but having to register games to an account to use them, and more worryingly requiring a constant connection just to play a single player game, is enough to warrant quite a few to be concerned about any potential purchase of the console.
Finally I would like to draw a comparison to some examples of online activation services used more by PC gamers such as ourselves, and what Microsoft should learn from the good and bad of these services. Steam is a great example of providing this service well, yes all games are attached to an account when used, but you can play games offline (although this has previously not worked very well), the other benefit is that unlike the Xbox One, Steam will not be replaced in X years by a follow up product, so I know my games will still be there no matter what. In contrast, a bad example, was the forced process that EA used to introduce Origin to the world, although the concept is similar to Steam, the way that it was forced with Battlefield 3, put the service on an immediate bad footing, add this with the previous history of EA pulling servers and you arrive to a very worrying prospect for EA games requiring Origin, especially when you add the fact that EA pulled most of its games from Steam following the release of Origin.
Overall the issue of digital rights, is one we will be watching closely and I know that personally unless the Ps4 announces similar efforts in future months, it is most likely going to be the console of choice for many frequent users.
Should Facebook do more to protect our freedom of speech?
Jillian York ask: with such a large number of users, should Facebook be obliged to protect our freedom of expression?
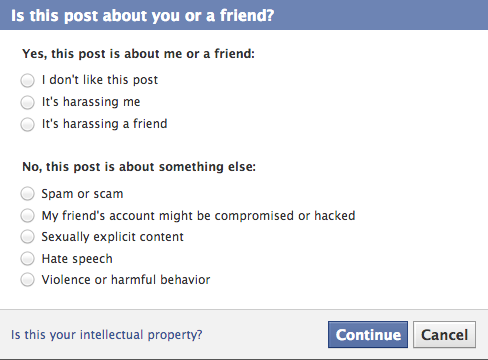
A few weeks ago, a number of women (and men) banded together in a successful campaign to challenge Facebook’s policies around content moderation, specifically the way in which the Internet giant has dealt with misogynistic content. In response, Facebook agreed that it would take steps to ensure that its policies toward dealing with such content would be brought in line with its policies toward other types of hate speech and violence.
The campaign brought about seemingly equal parts praise and disdain, with those in the latter camp—myself included—objecting primarily on the grounds that Facebook should not control speech.
But as Soraya Chemaly recently argued, the question of whether Facebook should moderate speech is different from whether the company should treat all types of hateful speech equally under their own policies. I agree with Chemaly when she says that “corporations … have a responsibility to treat hate based on gender in the same manner that they do other forms of hate speech.” Therefore, the debate is once again distilled into whether or not Facebook should be controlling speech at all.
Let’s break it down: Facebook has more than 1 billion users, 655 million of whom are active daily. The platform’s content moderation relies on what is known as “community policing”: In order for terms of service-violating content to be flagged to moderators, a user must first report it under a variety of different categories, including “sexually explicit content,” “hate speech,” and “violent or harmful content.”
After the content is flagged, Facebook’s team of moderators then reviews it. Just how many moderators are employed by the company, or what procedures they use for moderating the content remain a mystery: Facebook is notoriously opaque about their practices. What we can assume, however, is that—given the size of the platform’s user base—they’re spending less than a second on each piece of content.
A split-second may be enough to determine that an image such as those Chemaly’s campaign decries is abusive, certainly. But the myriad false positives over the years—such as a ban on the word ‘Palestinian,’ the removal of ‘Arab Spring’ activist pages, or the recent takedown of a page protesting genetically modified foods—expose a failed process.
Furthermore, the actual policies can be confusing. While few would decry a ban on images of abuse to women, Facebook also bans nudity and certain profanities, as well as pseudonyms (unless, that is, you’re Salman Rushdie).
Ultimately, while Facebook remains a private company, it has become the largest shared platform the world has ever seen, one that half the world’s Internet users employ in some way. At some point, we must consider whether that gives it additional responsibilities when it comes to protecting free expression.
Image: screenshot from Facebook
This does not apply to US citizens
US authorities claim that US data had not been under surveillance as part of the PRISM operation, Wendy M Grossman looks at whether there could be any truth to this.

"I don't worry about it," said my friend George at the tennis club when I asked him what he thought about PRISM and NSA spying. "I have nothing to hide."
It seems that George's life has been as spotlessly white as his blue-white English legs when it gets warm enough for him to wear shorts. No secret liaisons, no embarrassing moments he'd rather no one knew, no political affiliations to be nervous about…the only thing he could think of that he'd like kept private is his bank statement. I tried telling him that if you review the law books you'll find that most of us commit several felonies a day, but that didn't impress him either. I'm not sure he's ever even gotten a speeding ticket.
It was only after I said to him, "But what about other people?" that he began to look thoughtful. "Oh, yes," he said. "Other people. We must think of them."
The problem with so much of the US reaction toPRISM is that it focuses on what-plays-with-taxpayers. President Obama reassures the American public by saying that all this surveillance isn't about *them*; With respect to Internet and emails, this does not apply to US citizens.
Surveilling foreigners, apparently that's OK.
I had not realized until a couple of weeks ago that the attitude that citizenship confers rights that are not available to non-citizens is peculiar to Americans. Of course not: as an American I just assumed it was widely true. This idea was largely reinforced by experiences with the immigration authorities of other countries, who naturally see the right to enter or reside is theirs to confer or withhold. What I didn't realize was that immigration is a special case. *Human* rights are universal; that's the point.
As the privacy activist Caspar Bowden had to explain to me at ORGCon a few weeks ago, the rest of the world is up against the doctrine of American exceptionalism.
It's extraordinary that a nation of immigrants should be so persistent in viewing "foreigners" as lesser beings. And yet it's clearly a thread that runs through much of American life, from debates about whether illegal immigrants should be allowed to get drivers' licenses to the blanket refusal until 1968, when the Supreme Court stepped in, to allow dual citizenship.
I think the us-and-them attitude gets a book from the quasi-religious nature of how we're taught to be American, something I only really grasped when I took a second nationality. Under the First Amendment, the nation doesn't do school prayer and there is no established religion. Instead, nationalism takes the place of religion as a pervasive unifying bond. At the private school where I grew up, we said the Pledge of Allegiance to kick off school assemblies and sang "My Country, 'Tis of Thee". If you're trying to pull together a nation out of disparate ethnic and national groups, this makes a lot of sense as a bonding exercise. But the downside is to lessen the bonds with those in other countries who in other circumstances you might otherwise identify with as having common interests and goals. Americans of all stripes are outliers in so many ways: sports (baseball and American football instead of cricket and soccer), religion (American catholics often seem to have their own version of their faith), and so on.
This attitude is exacerbated by the sheer size of the country. If you are sitting in Nebraska, America stretches as far in every direction as the car can drive.
The big challenge for everyone outside the US, therefore, is to get across to them that what happens to foreigners matters in this story. For one thing, technically it's not really possible to implement mass monitoring of the flow of electronic data that only applies to foreigners, Data packets don't carry passports (or, in the metadata equivalent, have a field for "national origin of creator").
It will be some time before we can separate reporting errors and disinformation from the truth about the technical details of PRISM and the other recent revelations. But the documents published by the Guardian make it clear that determining whether data relates to US persons or not requires the retention and checking of a lot of ancillary information so it can be used to rule the data in or out. Basically, you're talking a giant database of US citizens. Even then, given the exceptions from the miminization rules for data about US persons, these processes provide little protection to either group. After all, that apparently blameless US person might have been the target of identity theft by one of those…foreigners.
Ultimately, the very fact that the infrastructure for surveillance exists means Americans won't stay safe no matter what guarantees are made now: its use will inexorably spread. Privacy activists call it "function creep". This particular consequence of globalization reminds me of a line from the early 1990s that we used about trying to censor the Internet: that it was like making a rule that you could only pee in the shallow end of the pool.
Wendy M. Grossman’s Web site has an extensive archive of her books, articles, and music, and an archive of the earlier columns in this series. Stories about the border wars between cyberspace and real life are posted occasionally during the week at the net.wars Pinboard - or follow on Twitter.
Image: This American Life Graphic Design Logo by Jeff McNeill CC BY-SA 2.0
Porn Summit Threatens Britain
Simon Phipps critiques the government's proposals on how to best deal with the issue of child pornography on the internet

The government clearly wishes to be seen to be doing something about the issues of children viewing pornography and of child pornography. To this end they have called a summit, to be chaired by Culture Secretary Maria Miller and attended by major Internet service providers including BT, EE, Facebook, Google, Microsoft, O2, Sky, TalkTalk, Three, Twitter, Virgin Media, Vodafone and Yahoo! Miller will aim to promote her view that “widespread public concern has made it clear that the industry must take action” and likely push for the Prime Minister’s stated objective to "put the heat on" ISP’s to prioritise the filtering and blocking of obscene and indecent material.
I’m sure you’ve seen some of the holes in this approach already. There are several glaringly obvious flaws with the very premise of this summit. Which is why I’m confident in stating that any solution devised by a summit built on this foundation is bound to harm the internet along with the freedom of its users.
First of all, if the summit is intended to regulate content, why has Mrs Miller invited only ISPs? That's like only inviting postmen to a summit about hate mail. Yes, some of these companies have attempted to make concessions to the government's approach by posting warning messages when certain sites are accessed or looking into filtering options, but they are making these ineffective gestures merely to assuage government zealotry. Something must be done. This is something. Therefore let’s do it.
They are unable to make a real contribution without infringing heavily on the rights and freedoms of other internet users because they are not the group responsible for the offending material. This is a fact to which politicians on both sides of the aisle seem to be impervious. No matter how the ISPs try to explain the logical holes in the argument, Miller and her ilk continue to assert that ISPs should be held responsible for the content they carry.
I called filtering an “ineffective gesture” in the previous paragraph and that’s exactly what it is. Porn filters are impossible because porn is subjective and filters are absolute. Demanding porn filters be imposed an all ISP customers is to demand use of a technology that randomly blocks arbitrary content or, worse, imposes the selective view of unaccountable individuals. Despite the trust placed by politicians in filtering systems like those used by the various mobile carriers. It’s clear that filters do not and cannot work.
Just this week, Open Rights Group has published details of ridiculous failures of filtering by the major providers. When Maria Miller talks about “filtering”, it’s these failures she wants to see applied by default to every internet connection in Britain. Worse, since these systems are all managed by private companies and imposed by private companies, there’s no oversight and no recourse for their customers. Getting a false block removed is almost impossible. Since every connection will have them, even switching providers is no remedy.
The meeting demonstrates clearly that the government has no clue what the internet does or how important it is to society. They appear to model it as a TV system, with regulated providers sourcing material for passive viewers. This overlooks its main value to society as a global nervous system in which contribution of content is as universal as its consumption. Legislators are still trapped by special-interest pleading over selected uses of the internet as a one-way channel for content, and as a consequence are contemplating laws that would utterly cripple that nervous system.
Their solutions all assume the providers select the content and can be instructed to do it differently. We’re all well aware that this is not the case, and that attempts to make it so will cause orders of magnitude more harm than they prevent. Long ago we decided the solution to hate mail was not to make the postman responsible for it. Why are today’s politicians insisting on the equivalent approach for the internet?
Follow Simon as @webmink on Twitter and Identi.Ca and also on Google+
The Halifax Regional C@P Association: The importance of youth, community and collaboration in the information age.
Laura Conrad looks at the importance of computer literacy education amongst students, with particular focus on the Halifax Regional C@P Association in Canada.

Most of them are young, but some are much younger than others. They work alone or in teams, in larger cities to the smallest rural corners of the region. Some of them will never meet each other in person, but they work together every day, towards achievements that are shared by communities across the nation and the world.
These are youth interns of the Halifax Regional C@P Association (HRC@P), a non-profit organization based in Nova Scotia, Canada, that takes a grassroots approach towards eliminating digital divides. The majority of interns being high school or first-year college students, the importance of their positions is often undermined; however, anecdotal and statistical evidence shows young adults as the most computer literate demographic of today.
Despite the many ups and downs the organization has faced over the years, Halifax’s C@P program highlights an issue of global importance: the need for community collaboration in addressing the complexities of the information age.
Defining HRC@P
Officially founded in the year 2000, HRC@P’s original intention was to create a network of community sites that provide internet access, in order to make use of information technology for the sake of social and economic benefits to the individual as well as the community. Despite the many twists and turns that unfolded over its 12 years of existence, the program continues to run successfully, to the great benefit of many social groups and individuals.
The program first intended to fund up 240 sites at various libraries, schools, recreation centres and other popular community areas. There are some sites that offer special services to favour certain groups such as seniors, youth at risk, individuals at risk of homelessness, and those with low literacy skills or learning disabilities.
HRC@P has struggled as an organization over the years by having to face the possibility of funding cuts. Each C@P site has typically received between $2,500 and $4000 in funding, from both the federal and provincial governments. This allows each site to determine where the bulk of the funds will be spent, depending on the particular community’s needs. This is what makes each site unique, and allows for the success of the program to be shaped differently by each community.
By 2012, the federal government withdrew its contributions to HRC@P, a $650,000 grant from Industry Canada. The provincial government, however, continued to commit its portion of the grant (approximately $348,000), allowing HRC@P to continue to employ approximately 200 students over the summer.
The role of the youth intern
Despite the funding cuts, some C@P sites have continued to flourish. A lot of this is dependent on the site’s distribution of resources, as the most successful sites were those with the financial resources to hire students or extra staff, as opposed to relying on support from volunteers.
This is important to note, as this is what highlights the importance of the role of the youth intern. The youth internship program is a fundamental component of HRC@P as it serves more than one purpose for communities; it ensures there is a staff person to administer the C@P program and to cater to the computer literacy needs of patrons, while also providing an opportunity for a young person to gain and/or leverage their computer literacy skills before entering the workforce. Young people use the internship as a means to connect to their communities in different ways. Some have developed innovative ideas to help the organizations they’re partnered with, such as by creating social media strategies or by holding tutorial sessions at their sites to teach basic web and software skills.
The interns work with minimal supervision, with the majority of reporting to supervisors being done via digital networking. They work in networks, connecting with their site supervisors during their shifts while also submitting weekly reports to those in management positions with HRC@P. Interns will also network with each other by sharing stories over Facebook Groups, Skype chats and blogs. By the end of each internship, students have gained a great deal of experience facilitating communication both internally and externally for a non-profit organization, using online tools to leverage their organization’s digital presence and soliciting additional funding on behalf of a non-profit organization.
Community collaboration vs. digital divides
C@P has been a successful program for several reasons; one of them being that it’s foundation is built upon community collaboration. The desire to learn is leveraged by the opportunity to connect with another individual, to share an experience from which both parties can grow. Many members of any given community are motivated to improve their computer literacy skills on account of the fact that doing so will allow them to become an integral part of a community operation, on which their participation is dependent for success.
Another reason why C@P has been so successful as a program is because its goals are focused on growth of computer literacy and digital education. The nature of technological growth in western society is now such that the younger generation is in a position to thrive; this is a result of a wide adaptation of technology in public education systems. According to a report recently released by Pew, 92 per cent of teachers have said the internet impacts their teaching abilities. In the same report, 73 per cent of teachers said their students use mobile devices to complete assignments, while 45 per cent use digital e-readers and tablets.
With this kind of education, young people are more equipped to address digital literacy issues within the community than ever before, allowing collaborative programs like C@P to thrive. Despite the harshness of the federal funding cuts last year, the program is still reaching its full potential because of the efforts and achievements of its youth interns. Like so many new developments in the digital world, the future potential of HRC@P is largely dependent on the younger generation.
When examining the benefits the program has had in Nova Scotian communities, it becomes clear why governments should continue to fund initiatives like HRC@P; it not only guarantees a culture of technology literate, empowered youth, but also allows all members of a community (even its most vulnerable) equal opportunities for progression in the workforce.
Prism Break
Wendy M Grossman looks at the issue of privacy policies, and suggests that the system must be 'fixed' in order for users to completely understand what information they are signing away.

The modern usability movement as it applies to computer software and hardware design began in 1988 when Donald Norman published The Design of Everyday Things. Norman, as he's patiently retold many times since, was inspired to write that book by six frustrating months in England, where he was constantly maddened because nothing, not even light switches, worked logically. His most recent book, Living with Complexity, looked at the design of complex systems, trying to pinpoint how to make the services we navigate every day less frustrating.
I was thinking of this recently, when the Open Rights Group hosted a meeting on the mid-May Sunday Times story that mobile network operator and ISP EE was sharing detailed customer data with the market survey company Ipsos Mori. EE and Ipsos Mori sent representatives, as did the Information Commissioner's Office. Essentially, they said a small pilot project had been misunderstood.
Privacy is a complicated issue because even experts do not have good answers to questions like how big a risk over what period of time is posed by the disclosure of a particular set of data. We know this much: today's "anonymized" data is tomorrow's reidentified data as more and more datasets come online to help triangulate it, much the way today's strong cryptography will be weaker tomorrow as computational power continues to grow. The ability to make accurate assessments is complicated by unknown externalities. How many users remember what they posted under which terms and conditions five years ago? And users themselves have varying understanding of what they think is happening.
We were into privacy policies and user consent, when I began to imagine what these might look like under a more stringent data protection law. It will be like today's omnipresent cookie authorization requests? Click OK to post this data. Click OK to share this data with our partner who just wants to sell you stuff. Click OK to let us reuse this data to personalize the video on the billboard you're about to pass. Click OK to…you mean, you didn't want to send your personal data to the US National Security Agency?
Which is when it occurred to me that we need better mental models of what happens to our data, and we systems designed to match them. Trying to convey this notion was difficult. Angela Sasse has been saying it to security people for 15 years, and what they hear is that users need awareness training. At the ORG meeting, what the group of people trying to say they have data privacy under control seemed to hear is that users need education and better-written privacy policies or maybe animations! But, as Norman has often written, a user manual – which is what a privacy policy is – is a design failure. What I meant was that if you could build an accurate picture of users' mental models you could then build systems that work the way users think they do so that the internal logic on which users base decisions is correct.
I am not suggesting we fix the users. The users aren't broken. Fix the *systems*.
The problem, someone pointed out to me afterwards, is that a lot of people think that their government knows everything about everyone anyway. But there's a big difference between that casual cynicism and seeing proof. Right on cue, the next day's newspaper headlines. The Guardian and the Washington Post say that under a previously unknown program called PRISM the NSA has direct access to the systems of US-based companies: Facebook, Google, Apple, AOL, Skype, PalTalk, and YouTube. (A number of these companies are quoted denying they have given such access.) Direct access as in, walk right in and pick the data they want. Also: the NSA is collecting the phone records of millions of customers of Verizon, one of the biggest US telcos. And: the UK's GCHQ has had access since 2010.
Worse, US government politicians are defending it: Democratic senators Harry Reid (Nevada) and Dianne Feinstein (California in the Wall Street Journal, President Obama in the Guardian. Charles Arthur has a helpful and rational decoding of all this and Nick Hopkins explains the UK's legal situation with respect to phone records.
At Computers, Privacy, and Data Protection earlier this year, the long-time privacy activist Caspar Bowden discussed the legal and technical framework for surveillance-as-a-service and the risks for EU users of cloud computing (which includes social media sites). Essentially, if there is a back door installed in these systems, "interception" is no longer a useful concept, and encryption is no longer a useful defense. Inside those data centers, data is perforce decrypted, and legally authorized direct access to stored uploaded data under the Foreign Intelligence Amendments Act (since the Fourth Amendment does not protect non-US persons) is not interception of communications.
Before the Internet, it was pretty simple to avoid being surveilled by a foreign country: you just didn't go there. So the first thing we need to make explicit in users' mental models is that uploading photographs and personal data to sites like Google and Facebook is digitally entering the US. We could start maybe by requiring large pictures of the services' national flag.
Wendy M. Grossman’s Web site has an extensive archive of her books, articles, and music, and an archive of earlier columns in this series. Stories about the border wars between cyberspace and real life are posted irregularly to the net.wars Pinboard - or follow on Twitter.
Turkey’s Twitter War
Aaron Stein looks at the importance of social media during the protests in Turkey.

After weeks of protests, Turkish Prime Minister Recep Tayyip Erdogan met with members of the Taksim Solidarity Group – an umbrella group for the demonstrators in Gezi Park – at his official residence in Ankara last night, in order to come to an arrangement to resolve the current crisis. The meeting lasted for several hours and the two sides appeared to have struck a tentative agreement to end the protests.
The meeting came on the heels of more tough talk from the Prime Minister, as well as an aggressive government led information campaign to relay the Justice and Development Party’s (AKP) version of events to the Turkish and international audience. The AKP has relied heavily on closely coordinated talking points that attribute the protests to a plot by “foreign circles" uncomfortable with Turkey’s economic and political progress. The government relayed its version of events via Erdogan’s frequent speeches, Turkey’s state-run Anadolu news agency, interviews wither friendly journalists, and social media.
The counter-information offensive was designed to combat the protest movement’s successful use of social media and to try and cast the protesters as marginal. To be fair, some of the flags flying in Gezi and Taksim suggest the penetration of a slew of radical leftist organizations, whose causes belie the portrayal of the protesters as apolitical youth solely intent on carving out a more democratic future. However, those groups are a small minority, of what is largely a leaderless spasm of anger at the AKP’s rule.
The protests began as a small sit-in style movement to prevent the razing of Gezi Park – a small park adjacent to bustling Taksim square. Protesters and some journalists chronicled the protests daily on twitter; posting pictures of excessive tear gas using the twitter hash tag #dailygasreport. The twitter campaign gradually gained traction, anger swelled, and eventually boiled over after Reuters photographer Osman Orsal captured the ghoulishly iconic image of the elegant woman in the red dress being sprayed at close range with excessive amounts of tear gas.
After the police did manage to clear Gezi Park, the subsequent brutal put-down of the peaceful sit-in at Taksim Square, which touched off two days of intense street clashes, was once again captured and broadcast to the world via social media. As the clashes unfolded, Turkish citizens had little choice but to follow the events live via twitter or Facebook. Turkish media outlets opted not to broadcast the events, choosing instead to air their regularly scheduled programing. CNN Turk, for example, opted to air a documentary on Penguins on Saturday evening, even though intense clashes continued in cities all through out Turkey.
Media outlets in Turkey are owned by large business conglomerates, dependent on government contracts for the financial well being of their numerous different subsidiaries. While the tight relationship between the media and the party in power is not new in Turkey, the emergence of social media has allowed people to circumvent the government’s attempts to stifle news coverage.
The AKP, while having embraced twitter to spread its own version of events, has not reacted well to the use of social media. In 2012, Ankara Mayor Melih Gokcek, sued 600 people on twitter for insulting him. Moreover, after the tragic bombing of a town near the border with Syria in May 2013, a local court banned coverage of the events and the publishing of images.
Nevertheless, images were quickly uploaded to social media sites and spread via numerous retweets, independent blogs, and Facebook accounts. For example, Elliot Higgins, the blogger behind the excellent Brown Moses Blog, created two databases of photographs and videos of the tragedy, in spite of the ban in Turkey and the local media’s inability to publish its own images. The Reyhanli coverage, therefore, foreshadowed the power of social media to circumvent the AKP’s media bans.
During the protests, Erdogan labelled social media a “menace” and a device to “spread lies.” Turkish police have arrested 25 people in the coastal town of Izmir for allegedly using social media to incite violence. In tandem, the Transport Ministry is now investigating twitter, claiming that “ [it] doesn’t have a legal basis in Turkey. They take ads but they do not pay tax in Turkey. It should establish a company compliant with the Turkish Commercial Code, like Facebook and YouTube.”
Despite these efforts, the number of social media users in Turkey continues to increase. However, rather than embrace the use of this new medium as a tangible expression of freedom of speech – which is guaranteed under Article 26 of the Constitution – the government appears intent on finding the legal justification to prevent the use of twitter. The AKP’s current legal effort to stifle twitter undermines its campaign rhetoric and its carefully cultivated image as the party responsible for the deepening of Turkish democracy. Thus, while the AKP may have a point about a small sliver of the protesters not being real democrats, its handling of the crisis, as well as its current effort further curb freedom of speech, is hardly representative of a party intent on deepening personal freedoms.
The AKP has a responsibility to protect the right to freedom of expression and should not shy away from embracing the growing use of social media. The party is the first in Turkey to have to govern in an environment where an increasing number of journalists, academics, and interested citizens are using social media to relay their thoughts about current events in real time. Thus, the party has a choice: It can either embrace freedom of expression and protect the use of social media, or it can opt to invent legal justifications to curb its citizens’ rights to freedom of speech.
If the government continues to pursue the latter of these two options, the AKP will have failed to embrace and embody its numerous campaign pledges to strengthen Turkish democracy. Moreover, it will have established a worrying precedent for future party’s to follow, should they be faced with a similar protest movement in the future.
Aaron Stein is a doctoral candidate at King's College London and a researcher specializing in Turkish politics at the Istanbul-based Centre for Economics and Foreign Policy Studies. He blogs at Turkey Wonk. Follow him on Twitter: @aaronstein1.
Image: Garden Inside Gezi Park by Gregg Carlstorm CC BY-NC 2.0
The world of Kindle
Milena Popova looks at how Kindle and Amazon are attempting to revive the world of fanfiction

So Amazon has decided to boldly go where… quite a few people have tried to go before actually, in its recent move to try to monetise the creative talent (or otherwise) of the fanfiction community. If you hang around fandom long enough, you realise that roughly every seven years someone pops up who thinks there’s a pot of gold at the end of the fandom rainbow, with this most recent effort very likely prompted by the success of the Fifty Shades of Grey trilogy which started life as a piece of Twilight fanfiction.
What differentiates Amazon from its predecessors in this field is that it has actually acquired the rights to – so far – three pieces of creative real estate. US-based fans of “The Vampire Diaries”, “Pretty Little Liars” and “Gossip Girl” will soon be able to write certain types of fanfiction for these shows and books and try to flog them to fellow fans with Kindles.
I say certain kinds because Amazon places quite a few restrictions on what you can and can’t publish as part of its Kindle Worlds initiative.Crossovers (works building on two or more existing universes, like Doctor Whooves – the Doctor Who equivalent of My Little Pony Land) are a big no-no, probably because of the rights headaches they would entail. Pornography and “offensive descriptions of graphic sexual acts” - a definition of which will presumably be expanded upon in the detailed content guidelines provided by each licensor - are also banned from Kindle Worlds. Given the prevalence of both crossovers and explicit erotic content in fanfiction, these choices on Amazon’s part are both understandable and likely to get the project dismissed outright by a large proportion of the fanfiction community. Though according to an Amazon spokesperson “Fifty Shades of Grey” wouldn’t count as pornography under their definition as it depicts “consensual sex between adults”. Amazon may be in need of a dictionary. Offensive content, including but not limited to “racial slurs” and “excessive use of foul language” is not permitted either. That’s right, Amazon wouldn’t publish the works of Mark Twain or Irvine Welsh.
Other mechanics of the scheme are also interesting. While Amazon state in their content guidelines that they do not accept poorly formatted books, quality control in this area is unlikely to include the services of a professional editor. Amazon Publishing is of course already full of poorly written, badly spelled crimes against literature. A little purple prose set in an existing universe, written by a thirteen-year-old figuring out the mechanics of writing is hardly going to make a difference here. Except when it comes to fanfiction, it will: there are already countless sites all over the internet where fans can get such stories – as well some excellent work that could easily compete with published authors – for free. From a reader’s point of view, Kindle Worlds hardly provides any added value in exchange for your $3.99.
And what’s in it for writers? Well, for anything longer than 10,000 words, Kindle Worlds will be offering royalties of 35% of the customer sales price. Shorter works of 5,000 – 10,000 words get you a royalty rate of 20%. What’s notable here is the copyright deal: in theory you keep the copyright to any original, copyrightable elements of your work. In practice, the minute you submit your story to Kindle Worlds, Amazon gets an exclusive license to it, and can then grant a license to your copyrightable elements (e.g. a new character) to the original licensor (i.e. the rightsholder of the universe you’re writing in).
The only way this can look attractive is if you haven’t been in fandom long enough to know your way around it; to know, for instance, that much like EL James and Cassandra Cla[i]re you can easily file the serial numbers off your fanfic and suddenly make 70% of the customer sales price rather than 35; to know that you’d be competing with work available for free; to know that what you’re doing counts as transformative under US law and thus the fact that Amazon hold the rights to the universe you’re writing in probably isn’t a huge amount of added legal value to you either.
Which brings us to the choice of properties Amazon has decided to partner with for Kindle Worlds. As has been pointed out elsewhere, one of the motivations behind the three particular worlds Amazon has licensed is that Alloy, the company behind all three, is a book packager creating cookie-cutter content, the rights management for which is probably easier than for works created by individual writers and then sold to media companies.
Yet, taking this from a different angle, they look like strange choices. “The Vampire Diaries” is perhaps the most obvious one, jumping on the bandwagon that brought us “Twilight” with its 200,000+ fanworks across the two major fanfiction archives (Fanfiction.net/FFN and Archive of Our Own/AO3). Yet “The Vampire Diaries” barely has 30,000 fanworks associated with it. “Gossip Girl” has a grand total of 483 on AO3 and zero on FFN, and “Pretty Little Liars” has just under 5,000 across both archives. There are more fics about the hung (ahem) Westminster Parliament of 2010 than in some of these fandoms. Thriving communities these are not.
What the three “Worlds” do have going for them is that they are all aimed at teenage girls and young women – precisely the kind of people who are likely to not have been in fandom for long enough to know their way around. This is where Kindle Worlds does potentially pose a threat to the fanfiction community. By convincing kids that the “right” and “legal” way to publish and read fanworks is through a paid-for, restrictive service, Amazon has the opportunity to shape the idea of what fandom is and how it works for a whole new generation of fans.
This is where the fanfiction community needs to step up. Yes, it’s easy to dismiss Kindle Worlds as the latest in a series of poorly thought-out attempts to cash in on fanfiction, and yes, we’ve collectively seen off plenty of the predecessors. However, what Amazon may actually be doing is deliberately sidestepping the existing community in favour of changing the game for the next generation. With any luck, the next generation will know how to use Google, and will find the free, unrestricted, and often deeply strange world of the fanfiction community before they find Kindle Worlds; but it never hurts to reach out and put up some signs pointing in the right direction. The Organisation for Transformative Works is already doing a fantastic job here, with projects ranging from the AO3 archive to legal advocacy, academic study of fandom, and the preservation of fandom history and at-risk fannish works. Now would be a good time for the community to further rally behind them.
Flow, sweet data, flow
Wendy M Grossman looks at the EU's plans to update the data protection directive.

It's very difficult to gauge the progress of the EU's attempt to reform the data protection directive, whose text is due to be agreed by the end of this year. Basically, it comes down to the difficulty of understanding what is going on in EU government at any given time. There seems to be more than 4,000 amendments (not exaggerating), an endless succession of committee votes, and little way to understand their order of precedence. Couple that general confusion over the EU's legislative process with the fact that a Mad Man trying his hardest could not have come with a term that sounded less engaging, and you have a subject that fights to get mainstream press attention.
At the beginning of the process, which will take until 2014 to complete, it hardly seemed to matter. A bunch of European regulators put forward plans to update the existing directive. The claim that reform was necessary seemed logical enough, since the directive was passed in 1995, when the Internet had only just been opened to commercial traffic, the Web was still a bunch of text pages listing links to other text pages, and the founder of Facebook was 11 years old. Yet what's opened up in the months since is the possibility that instead of a few tweaks and update we will get the substantial weakening of a law that offers European citizens some redress of the balance of power between themselves and the large organizations they transact with, often perforce.
The 1995 data protection principles have held up remarkably well, in large part because they *are* principles and not restrictions on specific technologies. Talk about robots and algorithm-driven decision making, for example, to a data protection expert and they're likely to see little difficulty in applying the principles to constrain potential damage to consumers and allocate liability. In that sense, the big change since 1995 isn't the advent of large, data-driven companies but global interconnection. In a world in which a public company the size of Netflix is built on Amazon's cloud services and, as Frances Cairncross predicted in 1997, distance is dead, the data you entrust to your local solicitor may be stored just about anywhere. How and where data may flow is one of the most contentious issues in the debates over reform, along with requirements for data breach notification.
Member states were required to transpose the directive into national law by October 1998 (the year Google was founded. By early 1999, as I see from my February 1999 piece for Scientific American (TXT)Simon Davies, then the executive director of Privacy International, went so far as to predict a trade war when US companies found themselves blocked.
“They fail to understand that what has happened in Europe is a legal, constitutional thing, and they can no more cut a deal with the Europeans than the Europeans can cut a deal with your First Amendment," he told me at the time.
Ah, yes, well, that was then. The EU and the US went on to negotiate a safe harbour agreement, and when the US wanted Passenger Name Record data the EU caved. Critical reports, such as this one from 2008 pop up in a search, and despite EU law, the US's big data data companies are demonstrating accelerating growth in the EU as elsewhere.
The EU law has been widely emulated. In 2000, Canada passed its equivalent law, PIPEDA. Meanwhile, the 2000s trend toward outsourcing means gave countries like India and the Philippines powerful motivation to copy the EU's data protection principles so they can sell call centers and other services to the EU. The US remains the outlier, stuck on its 15-year-old insistence on a free market approach - only now it has much bigger companies to finance lobbying efforts.
And there has been plenty of lobbying, both traditional and copy and paste. The latest, as the European Digital Rights Initiative documents, is questionable evidence built on assumptions that have no quantifiable basis.
It's a curious dissonance I wish someone would study in a PhD dissertation that data protection law has spread alongside increasing surveillance. Last week, Slate, under the influence of former Microsoft European privacy chief Caspar Bowden, argued that some amendments to the data protection directive have been written with US surveillance powers specifically in mind. Slate cites a report Bowden co-authored in January (PDF)studying the issues relating to cloud computing in the EU. Among the concerns raised by the report is the potential for the loss of control over the data stored in the cloud, as well as the fact that US companies offering cloud services are subject to the PATRIOT (2001) and the Foreign Intelligence Surveillance Amendments (2008) Acts. In other words, the US claims surveillance rights over EU citizens.
In other words: this dull-sounding labyrinthine process could cost EU citizens rights currently thought to be indelible. We'd better pay attention.
Wendy M. Grossman’s Web site has an extensive archive of her books, articles, and music, and an archive of all the earlier columns in this series. Stories about the border wars between cyberspace and real life are posted throughout the week at the net.wars Pinboard - or follow on Twitter.
Image: The European Parliament in Strasbourg by European Parliament CC BY-NC-ND 2.0

Latest Articles
Featured Article
Schmidt Happens

Wendy M. Grossman responds to "loopy" statements made by Google Executive Chairman Eric Schmidt in regards to censorship and encryption.
ORGZine: the Digital Rights magazine written for and by Open Rights Group supporters and engaged experts expressing their personal views
People who have written us are: campaigners, inventors, legal professionals , artists, writers, curators and publishers, technology experts, volunteers, think tanks, MPs, journalists and ORG supporters.





